Jeff Phillips, Code Siren, LLC
16 October 2023 - Technology / Code Siren
Introduction
Graphatars are a new and innovative technology with the potential to revolutionize the way we interact with the online world. They offer many advantages over traditional methods of digital identity management and conventional avatars, including enhanced privacy, security, portability, and convenience. Graphatars are generated from a unique post-quantum cryptographic-generated identifier and are not associated with personally identifiable information (PII). This pioneering cryptographic approach makes Graphatars highly resistant to identity theft and fraud.
Graphatars are portable and can be used across different servers and platforms. This portability feature is made possible as they are locally managed and owned by the user and not a centralized authority. This methodology allows users to export Graphatars wherever they go and still have access to their data and progress.
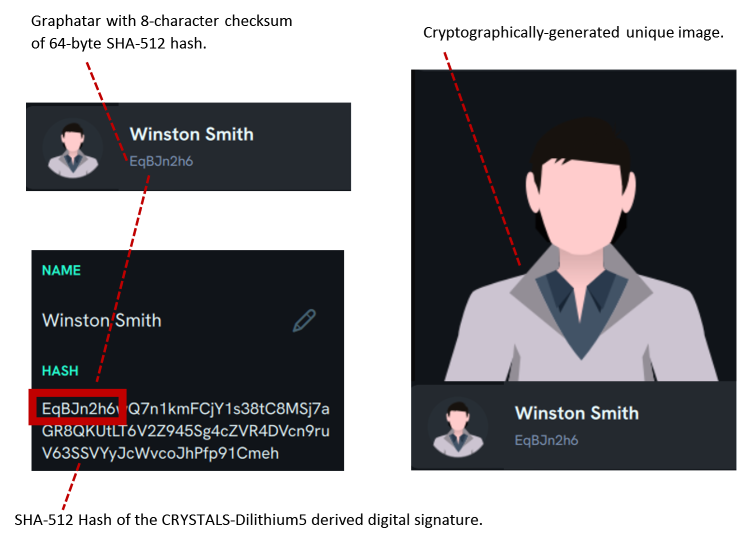
The key security attribute of Graphatars is that they can be used to verify a user's identity without requiring them to provide any PII. Since Graphatars are linked to the user's public key, which is publicly accessible, to verify a user's identity, someone only has to view the Graphatar and the mini-hash underneath the distinct thumbnail image to authenticate the user. Proper authentication techniques can potentially eliminate phishing risk wherever Graphatars are deployed.
Unique Identifiers
A Graphatar is a visual representation of the public keys of an identity. Graphatars are rendered as layered images that allow users to quickly determine if the person they are speaking to is who they think it is.
The Graphatar hash is a 64-byte SHA-512 hash of the Graphatar's CRYSTALS-Dilithium5 generated public keys. The Graphatar identifier is an 8-byte checksum of the 64-byte hash. These two hash values help analyze for possible threat actors, especially when a malicious individual attempts to impersonate a legitimate user.
Phishing Eliminated
Phishing and identity theft are major problems online. According to the United States Federal Trade Commission (FTC)
[1], phishing scams were the most common type of identity theft reported in 2022, accounting for 35% of all cases. According to the Identity Theft Resource Center's 2022 Annual Data Breach Report
[2], identity theft victims in the United States spent an average of 247 hours recovering from their losses in 2022. The total cost of identity theft to the US economy in 2022 was estimated at $52 billion. Globally, there were over 1,800 data breaches in 2022, exposing the personal information of over 422 million people worldwide.
Graphatars are the first line of defense against phishing and identity theft by minimizing the likelihood that an attacker can pretend to be another user, a vulnerability commonly found on other platforms, such as Discord, Telegram, Microsoft Teams, and Slack. Phishing on these platforms is a type of hacker-initiated scam in which attackers try to trick users into revealing their personal information, such as their login credentials, credit card numbers, crypto wallet private keys, or other personal details. Hackers may do this by sending users impersonating administrators or server owners messages or links or creating fake Discord and Slack servers or Telegram groups.
Your Identity Decentralized
Since the identity is owned by the individual (and not a centralized store or server), every Polynom server a user connects to will render the Graphatar the same across all servers. This process allows for an identity federation across disparate servers since the same public key(s) will verify all messages sent to those servers. Graphatar technology provides for authentication and non-repudiation. Not only does this allow all users across different servers to recognize a Graphatar identically, but it also allows messages sent to different servers to be verified as having originated from the same place, i.e., the person with access to the Graphatar's private keys.
How Unique is Your Graphatar Identity
Because there are over 15 Decillion (15,576,890,575,604,480,000,000,000,000,000,000) unique combinations, Graphatars make it mathematically impossible for attackers to trick users into believing they are somebody else. If a Graphatar does not seem right, such as the colors or characteristics of the image do not appear as expected, further analysis can be done by examining the Graphatar's identifier, the 8-bit hash. There are more possible Graphatar component combinations than the number of atoms in the observable universe.
Each Graphatar is generated using a mathematical algorithm with hundreds of variables. This algorithm takes a cryptographic digital signature as input and produces an image as output. The input is derived from the user's CRYSTALS-Dilithium5 digital signature, classified by the National Institute of Standards and Technology (NIST) as Security Level 5, the highest security level defined in NIST Special Publication 800-53, Revision 5. NIST describes Security Level 5 as "the highest level of security against all known threats."
[3]
The Graphatar algorithm factors every point, every angle, every layer, every hair color, skin tone, facial shape, hairstyle, clothing style and colors, ear lobe, and facial landmark as a mathematical representation of the user's CRYSTALS-Dilithium5 digital signature.
As we have demonstrated, Graphatar images are derived from hundreds of variables. The variables change randomly, driven by the value of the cryptographic key pair, generating a unique image. All of these values are changed by the user selecting a different image that best represents their selection.
 Each dot, guideline, facial landmark geometry, skin tone, clothing style, hairstyle, hair color, and clothing color represents a random variable generated by the CRYSTALS-Dilithium5 digital signature algorithm.
Each dot, guideline, facial landmark geometry, skin tone, clothing style, hairstyle, hair color, and clothing color represents a random variable generated by the CRYSTALS-Dilithium5 digital signature algorithm.
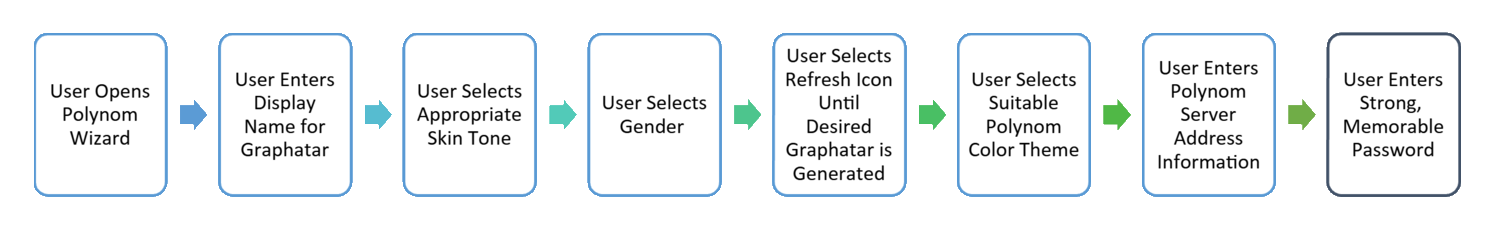
Step-By-Step Flow Diagram for Creating a New Graphatar
Real-World Applications of Graphatars
Enterprises could use Graphatars to provide their employees a secure and convenient way to log in to company systems and applications. For example, employees could use their Graphatars to access their company email, a file-sharing system, and a customer relationship management (CRM) system. This would eliminate the need for employees to create and remember multiple passwords and make it easier for the company to manage employee access to its systems and data while significantly reducing phishing risk from malicious outside parties.
A government agency could use Graphatars to provide citizens a secure and convenient way to access government services online. For example, citizens could use their Graphatars to file taxes, renew their driver's licenses, and apply for government benefits. This would streamline the process of accessing government services and make it more efficient for citizens and government agencies.
A bank could use Graphatars to provide customers with a secure and convenient way to access their bank accounts online. For example, customers could use their Graphatars to log in to their online banking accounts, transfer money, and pay bills. This would significantly reduce the risk of fraud and make it easier for customers to manage their finances.
Graphatars could replace traditional passwords and PINs for logging into bank accounts and other financial services. This would make it more difficult for hackers to steal user accounts and passwords. Graphatars could also verify user identities for transactions such as wire transfers and online payments.
Conclusion
Graphatars offer significant advantages over traditional methods of digital identity management and conventional avatars, including enhanced privacy, security, portability, and convenience. Unlike most universal identification technologies, Graphatar technology is a decentralized, user-centric, privacy-focused identification system that does not track user activity or engage in intrusive behavior.
Graphatars are the first line of defense against phishing and identity theft by minimizing the likelihood that an attacker can pretend to be another user.
Graphatars can provide users a secure and convenient way to log in to company systems and applications, access government services online, and manage their finances.
Overall, Graphatars have the potential to revolutionize the way we manage our digital identities by making them more secure, private, portable, and convenient for everyone.




 Read Other Blogs
Read Other Blogs