Code Siren, LLC Presents
Secure collaboration for
the post-quantum era
the post-quantum era
Future-proof your team's workflow and communications with the world's first decentralized, secure collaboration platform with military-grade security.
Community
Manage Groups
Designed for groups and communities wanting to take control of their own data. Self-host content, secure chats, and protect your privacy.
Community - Free Download
Enterprise
Minimize Costs
Purpose-built for companies that need a secure and compliant communication suite. It offers a variety of features that meet the needs of businesses of all sizes.
Enterprise - Contact Us »

Quantum Resistant
Collaboration
Polynom is a future-facing collaboration platform that uses the latest post-quantum cryptography (PQC) to protect your data from even the most powerful quantum computers. Polynom is CNSA Suite 2.0-compliant and uses a variety of security protocols, including AES-256 encryption, ML-KEM-1024 key exchange, SHA-512 secure hashing, and ML-DSA-87 digital signatures. Polynom also offers Social Encryption™ and Quantum Rooms™, which provide additional layers of security and ranks among the most secure collaboration applications.
FIPS 197 FIPS 180-4
FIPS 186, NIST SP 800-208
FIPS 203
FIPS 204
✔ CNSA Suite 2.0 Compliant
🛡️Social Encryption™
Social Encryption ("SE") is a quantum-resistant technology, allowing 1:n people to communicate E2EE across a network without manual key exchange. Any offline or online source of data can be used to initiate a symmetric key exchange, including passphrases, images, or any other files. By using shared experiences and knowledge to communicate E2EE, the network does not know that any data has been exchanged.
Social Encryption is a "rolling cipher" algorithm, meaning each row of entropy is derived from a separate source that's compounded into the final result - an AES-256 shared key. The final AES-256 key is used for end-to-end encrypting all content between parties. SE keys are identified across the network using an SHA-512 hash derived from an HMAC (hash-based message authentication code). This allows parties involved to know which SE key to use for the decryption without revealing any of the entropic data or secrets used to derive the SE keys.
Welcome
Self-Aware
Quantum Rooms™
Boost security and slash costs: Discover how Quantum Rooms and ephemeral data protects your privacy and bottom line ↳🛡️ Temporal
Based on quantum entanglement, the content in Quantum Rooms only exists as long as 1:n individuals view it. When the last user leaves, content self-destructs and the room ceases to exist. Quantum Rooms automatically merge disappearing content and private rooms without manually inviting users or managing authorizations.
🛡️ Autonomous
Quantum Rooms are do not exist in the traditional sense. They are not created nor are users invited to join them. Instead, they exist solely based on shared secrets and digital presence. This means that team members can discuss and share confidential data without worrying about manual deletion or expiration rules.
🛡️ Anonymous
Users without Social Encryption keys will not be able to see any Quantum Rooms, even if they exist. This means that someone could host an "Empty Server" without channels or rooms, and nobody would know about it. Only users with matching keys would be able to see which Quantum Rooms are available.
YOUR OWN MICROVERSE
World's First PQC Collaboration Suite
Enterprise grade security without compromises in convenience. Focus on building your company while Polynom handles the defense with unrivalled post-quantum cryptography and proprietary security.

PQC Chat, Groups &
Direct Messaging

PQC Voice Calls &
Conferencing
PQC File Vaults &
Datarooms

PQC ID & Role-Based
Authorizations

Phishing-Resistant
Announcements
See How Polynom Fares
Versus Other Applications »
BATTLEFIELD READY TECH
Deploy securely on both
private and public networks

Self-Hosting
Polynom gives users back their decision-making power. Instead of cloud services outside your control, self-host servers with your own rules and regulations. Almost any remnant device can be used for this purpose.
» See How Easy It Is to Own a CommunityDelegated Hosting
If you are interested in a less hands-on experience without any hardware requirements, we offer affordable and vetted delegated 2-click solutions through our verified hosting providers, such as ZeroEyes.
» Explore Delegated Hosting Plans⭐ Hiding in Plain Sight™
Polynom can operate on any network, regardless of its security posture. We use a variety of techniques to circumvent firewalls, generate random noise, and masquerade as other protocols, making it challenging to identify and block our traffic. We also utilize PQC exchanges to generate AES-256 keys, Quantum Rooms, and Social Encryption to further enhance our security.
» More On Polynom's Network ObfuscationIntroducing Graphatars™
Polynom uses cryptographically derived avatars, which are unique images that are generated from your keypair. These avatars can be used to visually represent you on Polynom, but they can also be used for more advanced security analysis. The use of cryptographically derived avatars provides an additional layer of security for Polynom users. By analyzing the hash and identifier of a Graphatar, it is possible to verify the authenticity of a user's identity and to detect potential threats.

Layered
Graphatars are rendered as layered images that allow users to quickly identify if they are speaking to the intended person. This makes Graphatars the first line of defense against phishing and identity theft by minimizing the likelihood of impersonation.
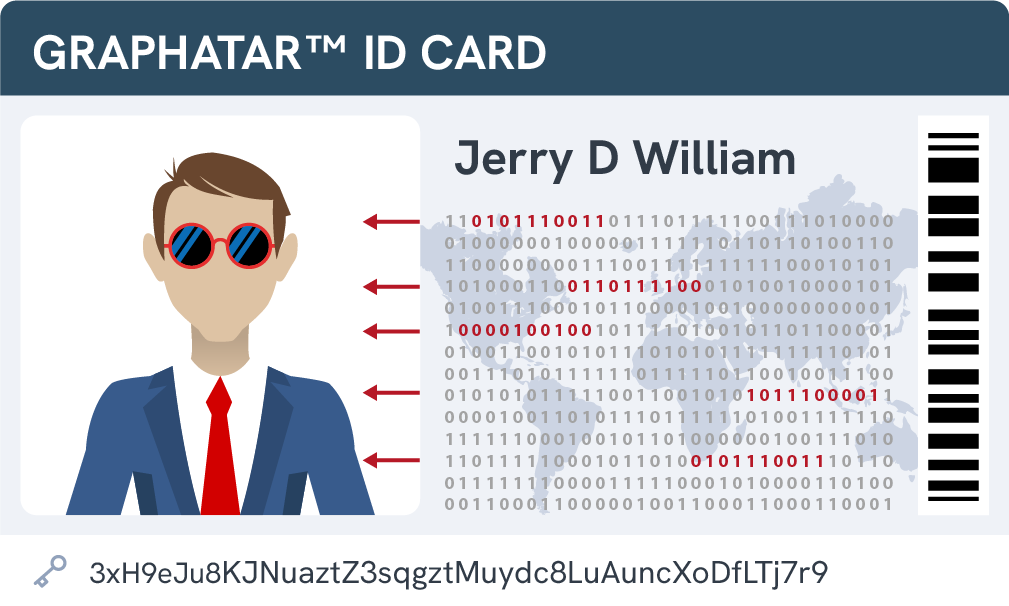
For Any Industry
The Graphatar engine lets you import personalized assets to each layer. Create branded IDs, bank cards, employee chips, virtual cards, membership & apartment complex passes, or even national IDs.
Marketing
Legal
NGOs
Education
Retail
Finance
Manufacturing
Healthcare
Software
+ 58 Industries
👋 Goodbye Phishing
Each Graphatar is unique and linked to the user's key pair. You can verify someone's identity by their public key or simply by looking at their avatar.
🕵️ No Sign-Ups or PII
You can create new IDs in seconds without providing any personally identifiable information (PII).
🔒 Full Ownership
Your IDs are locally managed and owned. You can switch servers or platforms and still have access to all of your data and progress.
🗝️ Role-Based Access
Polynom allows users to federate their identities across disparate servers, providing user authentication and non-repudiation.
😊 15 Decillion+ Variants
Supporting both business and casual looks. Selections for any gender classifications and guaranteed uniqueness that can't be replicated.
Choose from pre-created templates or create your own from scratch.
Reduce eye strain and read comfortably with custom fonts.
Familjen Grotesk
Hanken Grotesk
Switzer
Outfit
Supreme
+ System Fonts
+ Brand Fonts
+ Import Any Font of Your Choosing
Icon Sets and Shapes That Transform Experiences.
Modular UI. If you can imagine it, you can make it happen with our interface engine.
PEEK UNDER THE HOOD
Polynom™ Security Whitepaper - v1.93
UNLOCK POLYNOM'S POTENTIAL
Explore Polynom's Wiki for In-Depth Resources
A Peek Into Discord's Malware and Sinister Algorithms
Discord lurks in the flickering shadows of the internet, where pixels whisper secrets and whispers morph into malware ...
Continue Reading »
Telegram and Russia's FSB: An Uncomfortable Relationship
Telegram is the world's fourth largest instant messaging and VoIP app (after WhatsApp, WeChat, and Facebook Messenger), but the security ...
20 Min / Continue Reading »
What's Up with WhatsApp? – Most Used VoIP Security Critique
WhatsApp is the world's largest VoIP app. As of August 2023, it had over 2.74 billion active users worldwide. It is used by people in over 180 ...
15 Min / Continue Reading »
An Overview of Signal and Its Critical Vulnerabilities
Signal is a popular messaging app often touted as a secure, end-to-end encrypted platform created by respected cryptographer ...
10 Min / Continue Reading »
Read More at Blogs ↳
Industry News, Roadmap Updates, Product Reviews, Cryptography Analysis, and more.
Go To Blogs »
ZeroEyes
Delegated Hosting
Affordable, privacy centric and hands-off solutions for Polynom servers. Deploy without personal hardware.
Acquire Delegated Server »

Sublime Group
Outreach & Growth
Strategic collaboration for bringing PQC collaboration to demographics in traditional finance and DeFi.
Learn About Sublime »